Cloud, Cloud, Cloud everywhere. You may have heard this word every now and again. So yes I am talking about Cloud computing which has become one of the most talked-about technologies in recent years, with more and more businesses and individuals adopting cloud-based solutions to manage their data and applications. The concept of cloud computing refers to the delivery of computing resources such as servers, storage, and software over the Internet, rather than on-premises. This technology has revolutionized the way we interact with technology, enabling greater flexibility, scalability, and accessibility. With the rise of cloud computing, businesses of all sizes can now access powerful computing resources and software applications that were previously only available to large corporations with massive IT budgets. In this blog, we will explore the world of cloud computing, its benefits, and its impact on businesses and individuals alike. We will also discuss the various types of cloud computing models and services, and provide insights into how to choose the right cloud solutions for your business needs.
A quick overview
As cloud computing continues to evolve and mature, it is essential for businesses and individuals to stay up-to-date with the latest developments and best practices in order to fully leverage the power of this technology. By understanding the benefits and capabilities of cloud computing, businesses can improve their operations, increase their agility, and gain a competitive edge in their industry.
Cloud computing has become an essential technology for many businesses, as it allows them to quickly and easily deploy and manage their applications and data. Additionally, cloud computing has enabled the development of new technologies such as artificial intelligence, machine learning, and the Internet of Things (IoT), which have the potential to transform the way we live and work.
There are three main types of cloud computing models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). IaaS provides users with virtualized computing resources such as servers, storage, and networking. PaaS provides users with a platform for developing, testing, and deploying applications, while SaaS provides users with access to software applications over the internet.
Demystifying Cloud Concerns
Cloud security refers to the set of policies, technologies, and controls used to protect data, applications, and infrastructure in cloud computing environments. Cloud security is a critical consideration for any organisation that uses cloud computing services, as data breaches and other security incidents can have serious consequences.
Here are some common cloud security threats and examples of how to mitigate them:
Data Breaches: A data breach is unauthorized access to sensitive data. To prevent data breaches, organizations can implement measures such as encryption, access control, and security monitoring.
Account Hijacking: Account hijacking occurs when an attacker gains access to a user's credentials and uses them to access cloud resources. To prevent account hijacking, organizations can implement measures such as multi-factor authentication, password policies, and monitoring for suspicious activity.
DDoS Attacks: A distributed denial of service (DDoS) attack is a type of cyberattack in which the attacker floods a target with traffic to overwhelm it and disrupt its services. To prevent DDoS attacks, organizations can implement measures such as load balancing, firewalls, and content delivery networks (CDNs).
Insider Threats: Insider threats occur when an employee or other authorized user intentionally or unintentionally causes harm to the organization's data or infrastructure. To prevent insider threats, organizations can implement measures such as access control, monitoring for suspicious activity, and security awareness training.
Malware: Malware is a type of software that is designed to harm a computer system. To prevent malware, organizations can implement measures such as antivirus software, firewalls, and security monitoring.
How organisations deal with cloud security threats
Organizations that use cloud computing services need to have a comprehensive strategy for dealing with cloud security threats. Here are some common use cases of how organizations can deal with cloud security threats:
Use Encryption: Encryption is an effective way to protect data in the cloud. By encrypting data both in transit and at rest, organizations can prevent unauthorized access to sensitive data. For example, an organization may use an encryption service such as Civo provides SSL/TLS encryption for all inbound and outbound network traffic, which helps protect data in transit.
Implement Access Control: Access control is critical to preventing unauthorized access to cloud resources. Organizations can use access control measures such as role-based access control (RBAC) and multi-factor authentication (MFA) to ensure that only authorized users have access to sensitive data and applications.
Monitor for Suspicious Activity: Monitoring for suspicious activity can help organizations detect and respond to cloud security threats. By implementing monitoring tools such as AWS CloudTrail and Amazon GuardDuty, organizations can receive alerts when there is unauthorized access to cloud resources or other security incidents.
Implement Disaster Recovery Plans: Disaster recovery plans are essential to ensuring that organizations can recover from cloud security incidents. By implementing backup and recovery solutions such as AWS Backup and Amazon S3 Glacier, organizations can quickly recover data and applications in the event of a security incident or other disaster.
Security Awareness Training: Security awareness training is an important component of any cloud security strategy. By educating employees on best practices for cloud security, organizations can reduce the risk of human error and prevent security incidents. For example, organizations may conduct regular training sessions on password hygiene, phishing scams, and other security threats.
Introducing Rancher Desktop
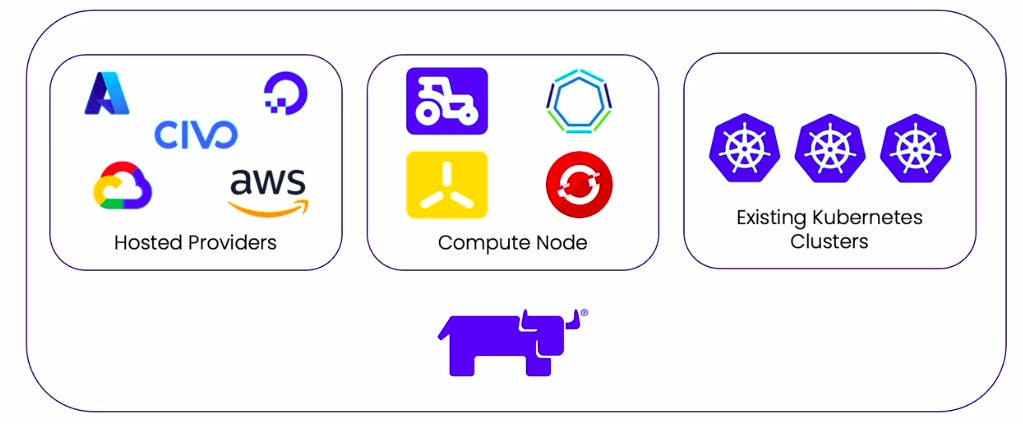
A complete configuration management platform for kubernetes
Rancher Desktop is a free, open-source desktop application that provides a local development environment for building and testing containerized applications. It allows developers to easily create and manage local Kubernetes clusters, and provides a simple way to deploy applications to these clusters.
Here are some of the key uses and benefits of Rancher Desktop:
Local Kubernetes Development: Rancher Desktop provides a lightweight, local Kubernetes environment that can be used for testing and development. This allows developers to work on their applications without needing to deploy them to a remote server.
Easy Cluster Management: Rancher Desktop provides an intuitive interface for creating and managing Kubernetes clusters. It allows developers to easily switch between different cluster configurations and versions, and provides tools for managing nodes and resources.
Application Deployment: Rancher Desktop allows developers to easily deploy applications to their local Kubernetes clusters. This makes it easy to test and iterate on application changes, and ensures that applications are fully compatible with the Kubernetes environment.
Integration with Other Tools: Rancher Desktop integrates with a variety of other tools and platforms, including Git, Docker, and Helm. This allows developers to easily integrate their existing workflows and tools into their local development environment.
Cross-Platform Support: Rancher Desktop is available for Windows, macOS, and Linux, making it a flexible and accessible tool for developers across different operating systems.
Through a simple user interface, you can configure how Kubernetes works. That includes:
Setting the version of Kubernetes you want to use
Choosing your container runtime
Configuring the system resources for the virtual machine (on Mac and Linux)
Resetting Kubernetes or Kubernetes and the container runtime to default with the push of a button
What wait for it, go check out their official docs page to try it out for your Kubernetes management and to secure it.
What we concluded so far
Securing your cloud infrastructure is essential to protect your sensitive data and prevent security breaches. With the increasing popularity of cloud computing, it is more important than ever to ensure that your cloud environment is secure and resilient.
To secure your cloud infrastructure the right way, it is important to follow best practices such as using strong authentication, implementing access controls, encrypting data, regularly updating and patching systems, monitoring for suspicious activity, implementing backup and disaster recovery, and conducting regular security audits.
In addition, it is important to use cloud security tools such as those provided by CNCF, and to choose a cloud provider that offers strong security features such as encryption, network security, and access controls.
Overall, by taking a comprehensive approach to cloud security and following best practices, organizations can ensure that their cloud infrastructure is secure and resilient, and that their sensitive data is protected from potential security threats.
